What is CEO Fraud?

Email has long been a core tool for business communications, whether it was directed internally, towards the employees or externally, towards suppliers, clients and other businesses.
Being such a vital tool for communication, the email is often subject to cyber attacks from hackers trying to steal your company’s money.
You may have heard of spam, phishing and spoofing as email threats to your data and computer, but have you heard of CEO Fraud?

Keep reading to find out what CEO Fraud is, discover 3 real-world examples and what to do to protect your company.
What is CEO Fraud?
FBI defines CEO Fraud as follows:
“A sophisticated scam that often targets employees with access to company finances and trick them using a variety of methods like social engineering and computer intrusions into making wire transfers to bank accounts thought to belong to trusted partners but instead belong to accounts controlled by the criminals themselves.” (source: fbi.gov)
This fraud is targeting businesses working with foreign suppliers and/or businesses that regularly perform wire transfer payments.
The scammers don’t discriminate: they target large corporations as well as small to medium sized companies.
This fraud originated in Nigeria but has spread throughout the world.
[bctt tweet=”In the last year, FBI reported the loss of over $3.7 billion due to CEO Fraud.” username=”brand_minds”]
How does CEO Fraud work?
The cybercriminals hack the email of an executive and use it to send email messages to a targeted employee working in the financial or accounting department. The impersonating message contains instructions to transfer funds to a specific bank account controlled by the scammer.
Why is this type of fraud so dangerous?
Using deception, the cybercriminals make the emails look credible and familiar. The employee doesn’t suspect it as being fake for a second. Because the scammers are leveraging the influence and authority of a top executive or CEO, this type of fraud came to be known as the CEO Fraud.
Here is a sample of an email designed to trick the targeted employee:
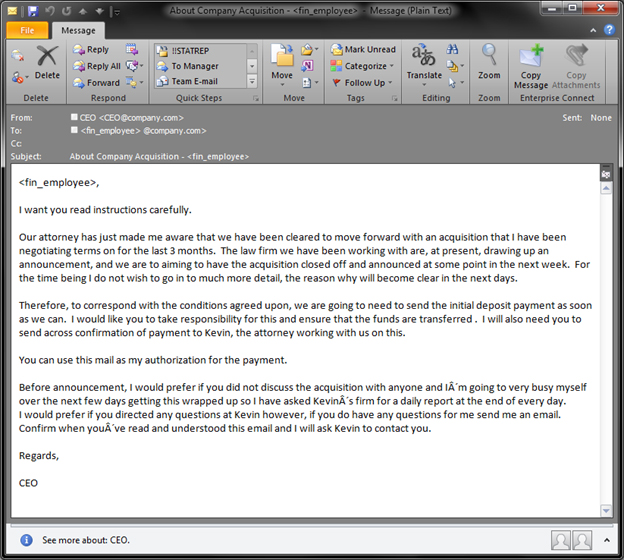
source image: blog.trendmicro.com
3 real-world examples of CEO Fraud
-
Etna Industrie, France
Etna Industrie employs 50 people and has been making industrial equipment on the outskirts of Paris for nearly 75 years. In 2016, the company became a victim of CEO Fraud.
The company’s accountant received an email from her boss, Carole Gratzmuller announcing that she was buying a company in Cyprus. The email included instructions from Carole as to where to transfer the money.
A total of $542,000 was transferred to foreign bank accounts: the banks held three of the wire transfers up, but $142,000 went through to the scammers. (Source: bbc.com)
-
FACC Operations GmbH, Austria
FACC Operations GmbH is an Austrian company that produces various airplane parts for companies like Airbus and Boeing.
In 2016, the company announced that it was the victim of a cyber fraud that targeted its financial accounting department.
The financial damage was at $54 million. (Source: news.softpedia.com)
-
Mattel, U.S.A.
Mattel, the well-known manufacturer of the Barbie doll has fallen victim to the CEO Fraud as well.
In 2016, Mattel was pushing to increase its business in China and had a new CEO at the helm. An executive in the finance department received an email from the newly appointed CEO to wire $3 million for a vendor in China. Mattel has a double-check transfer system in place that each payment must go through.
The payment checked out correctly and the executive wired the funds. Hours later she mentions the money transfer to the CEO who denies having sent such an email.
Mattel quickly asked the help of the Chinese Police which was successful in recovering the money two days later. (Source: news.com.au)
Expert’s Opinion
We talked about CEO Fraud to Mihaela Paun, Bitdefender’s Vice President of Consumer Sales and Marketing.
Here are her recommendations:
“Two major factors converge to the success of CEO fraud: the social component that prompts the employee to comply with the request under the hierarchic pressure and the amount of money that cyber-criminals can make in one shot.
This is why advanced security measures should be complemented by strong internal policies at all times. On the technology side, several aspects financial departments (or any department that works with payments) should take into account are the use of two-factor authentication mechanisms and close monitoring of internal communications impersonating executives. Spam traps can be trained to raise alerts with IT security whenever the sender’s name does not match the associated company e-mail address. E-mail coming from “typosquatted” (impersonating) domain names should be discarded immediately by the antispam filer as well.
On the human side, financial departments should implement strong payment policies. Payments should not be made in the absence of an agreement or purchase order associated with the invoice. The purchase order should clearly state the beneficiary, the maximum amount of money and the bank account number for the payments to be made to. For large amounts of money, extra approvals should be formalized and double checked offline such as calling a trusted phone number.
Security of transactions should be an ongoing effort and every employee should be trained on how to spot phishing attempts, as well as how to report such attempts to the IT department.”
How is your company protecting itself from CEO fraud?