Top 4 Security Vulnerabilities You Might Not Be Aware Of
Is your company vulnerable to security threats?
Security threats can put your organization and your customers’ sensitive information at risk. Remember the WannaCry ransomware attack that was deployed in May 2017? The attack was estimated to have affected more than 200,000 computers across 150 countries, with total damages ranging from hundreds of millions to billions of dollars.

This article points out 4 security risks and helps you protect your company against them.
[bctt tweet=”Discover 4 security risks you might not be aware of” username=”brand_minds”]
Here are our top 4 security vulnerabilities:
1. Networked printers.
Network printing helps users share print resources around an office or building. There are many benefits to network printing, but it also has one major drawback: it is vulnerable to online attacks. If your printers have outdated firmware, they are potential tools for espionage and data theft. They are a gateway to your company’s network and can be used as a springboard to launch other attacks.
Solution:
- Make sure your company’s printers have updated firmware;
- Set up systems to update them on a regular basis;
- Isolate printers on restricted network segments allowing access only to a dedicated print server.
2. Internet of Things (IoT).
From your fridge to your air conditioning systems, IP cameras and coffee machines, they’re all connected to the Internet. The purpose of the Internet of things is to help us save time and make our lives easier and more efficient. But cyber criminals can also turn it against us. They can use any of the connected devices you have in your home to steal personal data, to vandalise and remotely compromise your property.
Solution:
- Implement firmware updated and patching cycles;
- Isolate these devices into their own network segment.
3. Ageing infrastructure
Devices making up your infrastructure reach the end of their useful life. Are you aware which of your infrastructure devices are end-of-life products? Because the respective devices can no longer be updated with the latest software or hardware, your company runs the risk of online attacks and compromise.
Solution:
- Track your device purchases and know their end-of-support dates;
- Have your devices budgeted to be replaced before the end of your last support period.
4. People
One of the biggest gateways to your company’s assets might be your own employees.
People like convenience and the easiest path, which means they constantly create vulnerabilities in your organisation. The CEO fraud is one example of how people can be manipulated and influenced: read our article.
Solution:
- Train your employees regarding security awareness on a regular basis;
- Inform them of the latest cyber attacks and educate them on how to protect themselves against them;
- Include security awareness in your company culture.
Security is no longer about installing antivirus software and hiding the company’s network behind a firewall.
A strong security foundation is paramount if you wish to maintain your company’s reputation and longevity.
Gmail’s Makeover And How It Can Influence Your Working Habbits
Google gave Gmail a big refresh that will change the way you interact with it and help you even more than before. As first reported by The Verge, the upgrade was revealed in a message from Google to administrators of G Suite accounts. The message stated that the changes would be coming to consumer Gmail accounts, as well as G Suite accounts.
The redesigned Gmail web interface is focused on quick productivity actions. Google is introducing features such as attachments chips, hover actions, and hover cards to make the static inbox experience more interactive without the need for multiple clicks. Google is also surfacing several labs features that were previously hidden in Settings > Labs, like canned responses, the ability to create multiple inboxes, and a preview pane to customize your preferences for different inboxes.
According to Fox News, Gmail is getting deeper G Suite interactions to directly create and edit Google Calendar invites, send notes to Google Keep, and manage to-do items in Tasks. “Google is also releasing new Tasks mobile apps for Android and iOS for adding and editing tasks from your smartphone to manage in Calendar and Gmail. The Tasks app is available today in the iOS App Store and Google Play Store. Aside from the new-look web app and Tasks mobile apps, Google also announced new security features, including Gmail confidential mode, and expanded AI capabilities like smart replies and notification priority settings,” added Fox News.
Here are some of the main changes and how they will impact you
Smart Replies and Smart Filtering
New AI-powered features in Gmail, like Nudging, Smart Reply and high-priority notifications, can now help you spend more time on work that matters. With Nudging, Gmail will proactively remind you to follow up or respond to messages, making sure you don’t drop the ball.
Smart Reply offers pre-set, one-line replies for any email. The replies are not just standard answers, but customized according to each email, due to machine learning, that suggest responses to you, in order to help you save time. Moreover, two new features promise efficiency improvements through smart filtering. Notifications for high-priority messages help you focus on your most important work. From now on, Gmail will pay attention to frequent newsletters and suggest you give them the boot by unsubscribing if you stop opening them.
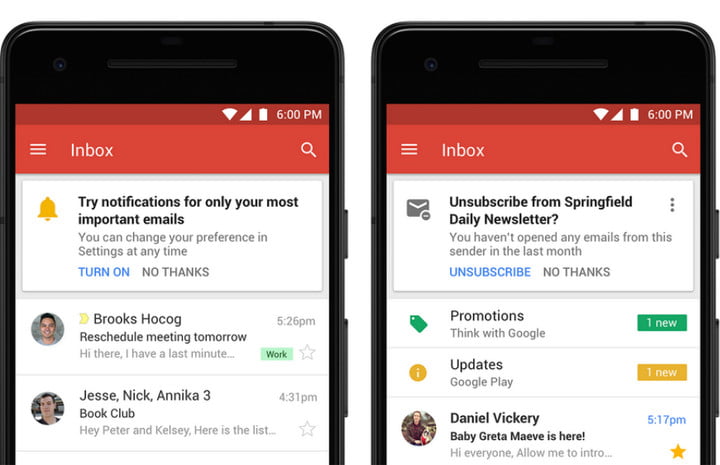
Protection from risky emails
Built-in Information Rights Management (IRM) controls also allow you to remove the option to forward, copy, download or print messages. This helps reduce the risk of confidential information being accidentally shared with the wrong people. Confidential mode will begin to roll out to consumer Gmail users and a limited number of G Suite customers in the coming weeks (broader rollout following).
Moreover, the redesigned security warnings within Gmail are simpler to understand and give a clear call to action to employees. These bigger, bolder warnings will help you be even more informed when it comes to potentially risky email.
“When you compose sensitive email you can remove options to forward, copy, download, or print the messages. The option to protect your outgoing email with two-factor authentication — the recipient needs to log into their own email and click to receive an unlock code via SMS text to read the message you sent could help you sleep better at night if you later discover their email account was hacked,” wrote Digital Trends.
Icons for Action Buttons
In the old Gmail interface, you’ll find the action buttons in the inbox along with a text label. In the new interface, Google has turned these action buttons into icons — you can’t read any text labels anymore. Also, this new icon menu has got two additional actions for quick access: Mark as read/unread and Snooze.
New Sidebar
It shows icons of other Google services like Calendar, Keep and Tasks. Tapping any icon expands the sidebar allowing you to quickly access your calendar entries, notes or tasks synced to your Google account. Any changes you do in these apps is synced back to the cloud and is instantly accessible on your other devices. You can also access third-party Gmail add-ons from the same side panel.
New native offline capabilities in Gmail on the web can help you work without interruption when you can’t find Wi-Fi. Search, write, respond, delete, or archive up to 90 days of messages, just as you would working online, but offline.
You can use Tasks to create tasks and subtasks, and even add due dates with notifications to help you stay on track. And because Tasks closely integrates with G Suite, you can simply drag and drop an email from Gmail into Tasks to create a to-do. Tasks with due dates can also appear in your Calendar. You can download the new Tasks mobile apps from the Google Play Store or iOS App Store today.
Different Display Modes
According to Economic Times, Google has added three view modes: default, comfortable and compact. Default view is ideal for large screens where you can open the preview of attachment in an email right from the inbox. This means you don’t need to open the email itself. Comfortable view is great for laptop users – it has large text which is easy to read sans the preview option of the default view. Compact view is the same as before.
Gmail versus Outlook: which e-mail provider is better for you? Part II
Last week we started a bigger discussion about the best two free email providers – Gmail and Outlook – and which one might be the best to choose from your business. Now, we continue and elaborate the subject.
5 Advantages of using Gmail
- Productivity– It comes in handy when you are looking to enrich your productivity. Some of its many features is the built-in tasks utility that you can use to send tasks to your Google Calendar.
- Easy usage – The provider is very user friendly. Anybody would get used to it pretty fast.
- Customization– Gmail allows for a great deal of customization. Not only can you control the appearance of the Gmail interface using themes, you can choose the way your inbox works by turning features such as tabs off and on. Also, use color coding and markers to customize how various messages appear.
- Integration– Gmail integrates with a number of other Google tools. There are also many Plugins that expand the capabilities of Gmail even further.
- Community Support– The Gmail help center is well-organized and addresses many questions. Plus, Google maintains a Gmail help forum, where users can ask specific questions.
5 Advantages of using Outlook
- Ease of Use– com is easy to download and use. It has a clean, modern interface that is intuitive and easy to understand.
- Productivity– Outlook has a built-in task tool. You can easily access the calendar from within your inbox by clicking the Calendar icon and without leaving your inbox.
- Customization– As with Gmail, you can use themes to change the appearance of your interface. You can make some limited changes to the way that your inbox works, such as choosing where the reading pane appears and choosing to show or hide preview text.
- Integration– it integrates with other Microsoft tools. You can use the grid in the upper left of the inbox to open other Microsoft tools. There are also many add-ins that expand your email capabilities. You can add them from within your inbox using the Manage Integrations option.
- Community Support– Outlook for MS Office is widely acknowledged as the standard in many corporations. Outlook.com also has a user community. Plus, there are many helpful third-party articles and tutorials written that can help you anytime.
Ultimately, choosing your email provider is a very intimate decision and it must be based on your work and personal preferences. A free email service like Gmail or Outlook.com can be a good choice for you or your small business.
Before finalizing your choice of email providers, it’s important to ask yourself what you really need from your email service, address the main important questions regarding your type of business, dimension, usage, security, how many people will be accessing it, etc. The email service you choose depends on how you use your email and what you need from it. If you approach the decision carefully and make an informed choice, the email provider you choose is likely to be the best email service provider for you.
In other words, no matter how many pieces of advice you receive, the decision belongs to you. Because while some consider Outlook to be an upgrade from Gmail, others still see Gmail as the king of the free email providers.
Here is an opinion about why leaving Outlook for Gmail, while here, an opinion in reverse.
Decided? What will you choose?
Gmail versus Outlook: which e-mail provider is better for you? Part I
According to a Radicati Group study from January 2017, there will be more than 3.7 billion email users worldwide by the end of the year. That means that nearly 54% of the entire planet is currently using email. Putting things in perspective, the same group reported about 1.9 billion worldwide users in May of 2009 and projects that that number will reach 4.1 billion by 2021.
According to wikipedia, Gmail dates from 2004, but Official Gmail Blog tracks the public history of Gmail from July 2007. In February 2016, Gmail reporter 1 billion monthly active users, up from 900 million the company announced during its I/O developer conference in May 2015 and up from 425 million in 2012, says TechCrunch. Outlook was re-launched by Microsoft in 2012 Microsoft migrated all Hotmail users to Outlook.com. The fledgling service has a ton of unique features including Clutter, email rules, and integration with Outlook calendar. In early 2017, Outlook.com had a reported 400 million users. However, that number hasn’t changed as drastically as Gmail’s statistics. In July 2011, Microsoft was said to reach 360 million active users for its Windows Live Hotmail service worldwide.
The Radicati Group counts the 3.7 billion email users in January 2017 as both consumer and corporate users. However, because it isn’t clear how the email accounts are differentiated between consumer and business users, it’s hard to measure the accuracy of the statistic.
Therefore, we decided to take a look at the most important two email providers: Gmail and Outlook, and give you the possibility to have a clearer picture on which one you would prefer better. Both Gmail and Outlook offer both free and premium versions. The premium email versions have, naturally, more features.
| Google’s Gmail | Microsoft Outlook.com | |
| Storage | 15 GB. The storage limit is shared between Google Drive, Gmail, and Google Photos. If you’ve reached your limit you can buy extra storage. Your Google Account also has storage in the cloud-based Google Drive. | While the actual limit is unclear, it appears that you start with 5 GB of storage and this amount increases over time. Your Microsoft Account also has storage in the cloud-based OneDrive. |
| Search Capabilities
|
Search any combination of the following elements using the advanced search:
|
Outlook.com has a simpler search. The search mail or people option allows you to search any combination of:
Or you can search your contact list. There is a separate search for Skype as well.
|
| Security | Includes 2-Step Verification and spam detection. You can enable a verification icon for emails from verified senders through Google Labs. | Includes 2-Step Verification. Uses trusted sender icons for emails from trusted senders. Suspected spam messages appear with colored red or yellow safety bars at the top of the message. |
| Inbox Organization
|
Default Gmail organization is based on labels and up to five tabs. Assign colors to labels and use stars and other symbols to flag important messages. Also, you can convert your inbox to a classic inbox or a priority inbox. | Default Outlook organization is based on categories, folders and subfolders. Flag important messages or pin them to the top of the folder. |
| Instant Messaging | Gmail uses the Chat function for instant messaging. You can find the Chat icon towards the bottom of the Gmail inbox on the left. | Outlook uses Skype for instant messaging. You can find the Skype icon in the upper right corner of your inbox. |
| Contact Management | Import contacts from a variety of other email providers including:
Import a CSV or vCard file. Import contacts from your Google+ social media account. |
Import contacts from other sources, including:
|
| Advertisements | Ads appear as emails at the top of your inbox tab. The word “Ad” appears in a yellow box to the left of the subject line. | Outlook.com uses display ads that appear to the right of your inbox. They take up quite a bit of space on the screen. |
| Extras | Incorporates tasks, customizable themes, Google Lab. | Incorporates calendar, tasks, customizable themes. |
source: Business Tuts Plus
Head to head
Calendar
As process.st points put, neither platform has a real solution that lets you view your calendar and email side-by-side. While both Gmail and Outlook sync events with your calendar, neither let you view your calendar and inbox at the same time, in one tab. When you click on the Outlook tool bar, you’re taken to a separate calendar window. On the other hand, when you click on Calendar in Gmail, it keeps your inbox open, and adds a new window (or tab) with your calendar.
Neither Gmail nor Outlook lend well to multi-window viewing. At least Gmail lets you view your calendar and email at the same time.
User Experience (UX)
Text in Gmail is larger than in Outlook. Coupled with the clear definition between bold and non-bold text, as well as the inbox shading available with most templates, Gmail is generally softer on your eyes. So if you are spending a lot of time in front of the computer, you might prefer Gmail on this one. Moreover, the provider is very useful when it comes to unread emails. “Read” emails appear in a darker shade than “unread” ones. “Unread” emails are also distinguished, because their sender and subject are in bold.
Outlook differentiates these by putting the sender and subject in blue. It’s bold too, but since the text overall in Outlook is flatter and smaller, you still need to squint to see if something is a new email. More opinions you can find here.
Filters & Organisation
Besides the already known features, lifehacker.com, points out that Gmail uses labels and stars instead of folders (although it has faux-folders, too.) You can apply multiple labels to your messages, which gives you greater flexibility in setting up exactly the kind of organization scheme you like, and stars let you set aside the most important emails for later. You can even enable Smart Labels that Google can apply labels like Finance and Travel automatically.
Gmail also uses a priority inbox system to automatically find messages it believes are important to you. Emails are deemed “important” based on who you email, which messages you open, what you interact with and other criteria. You can also manually mark an email as important to help it learn.

End of part I.
How to choose the best antivirus software for you – Part II
We continue the list of pieces of advice that will help you take a very documented and precise decision while choosing your antivirus software, after last week’s article.
According to pcworld.com, to find out about the biggest names in antivirus, you should visit AV-Test’s Windows home users page. Here, you’ll find a breakdown by Windows version, with each program rated on three criteria: protection, performance, and usability. The companies are listed in alphabetical order, but you can click on any of the criteria points to get a ranking based on that (performance, for example). Each category is rated on a six-point scale represented by a group of circles. More colored-in circles means a better score.
According to heimdalsecurity.com, 3 ways you can find the best free or paid antivirus for you are through: user opinions, expert reviews and independent testing.
Cybersecurity forums are still some of the best places you can check to find good and trustworthy reviews and comparisons of antivirus software. You may also use Quora (The website is designed so you can quickly access your areas of interest. You can ask a question or just simply browse it looking for your areas of interest), yahoo answers (centers on the experience and knowledge of everyday users rather than the knowledge of experts), reddit (Ask Reddit users to compare various antivirus software and you will end up with a very lively conversation among users that covers almost every antivirus program imaginable. ‘Redditors’ will talk at length about the pros and cons of one antivirus or another.), trustpilot (Reviews of antivirus programs are another way to choose the product that fits your needs. Most people read the reviews on the developer’s page, but it’s impossible to be sure which review is real and which isn’t.).
The next step would be looking for the experts’ opinions, that are well-documented.
Paid-for antivirus software
Many people keep their computer safe by paying for a security suite, which will usually include antivirus software, protection against scams and a firewall. Most brands have options for just one device or, for more money, multi-user licences so you can install the same protection on two or more computers in your home. Some also allow you to pay extra up-front for a further year or two of cover.
Pros: Provides an all-round security solution accessed through a single interface. Individual components are automatically updated at the same time so you get protection against the latest threats. Cons: They can be expensive and you’ll also face ongoing costs, usually in the form of an annual subscription, to receive updates after the initial period of protection is over (usually a year). Some security suites can place a drain on system resources, too, potentially slowing down your computer.
Pay attention to the performance
Security products are, by nature, programs that require quite a bit of computing resources in order to do their job. They will definitely use more computing power than your media player, for example. If your computer is not the most powerful on the market, you should take into consideration the performance aspect:
- Have a small impact on the boot timings of your computer. Your Windows should start almost as fast as it did before you installed your security product.
- Have a small impact on your computer’s performance. A very effective security solution is no good if it bogs down your computer. A good security product will know how to use your computer’s resources in a way that doesn’t negatively impact your computing experience in terms of performance and responsiveness.
- Be fast in scanning your computer for malware. Good antiviruses tend to be faster than others when it comes to scanning your computer for malware threats.
When choosing the right security product for you, you should check whether the additional tools are:
- Security-oriented. If a security product gives you for free additional tools that are not security oriented, we believe that they are not worth buying. Those tools are probably just a means to a marketing end.
- Useful. Whatever they do, the additional tools you get when buying a security product should be useful to you. They shouldn’t be just clones of tools that are already found in Windows.
- Don’t harm your security or your privacy. Some vendors choose to bundle additional tools that are not helpful in increasing your security or privacy. On the contrary, they are harming it. If a security solution includes shady toolbars, web browsers, browser add-ons or any other tools that lower your security or privacy, you should stay away from that product.
- Don’t involve additional costs. If you need to pay more money in addition to what you already paid for the security suite, they’re not worth it.
Usability is key
According to Digital Citizen, a good security product must be easy to use both by knowledgeable users as well as casual users with little to no knowledge about security. Here are some of the facts that they are pointing out:
- Be easy to navigate. A good security solution should provide you with an intuitive way of navigating through its various windows, tabs, menus and settings.
- Be easy to use on devices with touchscreens. The era of the plain old monitor is dead. These days, the number of PCs with a touchscreen on them is increasing at a very fast rate. Thus, more and more people use touch in order to control how software works. A good security product should have large buttons, tiles, switches of all kinds, check marks and so on – control elements that are easy to touch with your finger too, not only with a mouse’s cursor.
- Be easy to understand. No matter how easy it is to navigate through a user interface, it’s no good if you don’t understand what each and every item and setting means. The configuration options that are offered should be easy to understand by all users.
- Be easy to configure. Good products are products which are easy to set… not like those at IKEA :). Security products should be easy to configure.
- Provide you with easy to find documentation. Just like any good product, good security products must provide an easy way to access their documentation. If Help documentation is available but you can’t find it, what’s the point?
- Give you complete control of how it works. Many people look for security products that don’t require any special configuration. But there are also people who want to set each and every detail of how a security product works. If that’s the case for you, a good security product must provide you with complete control.
According to heimdalsecurity.com, “ no single antivirus solution is enough to keep you safe. Even antivirus developers encourage you use multiple security software programs to keep you safe. If malware passes one software, they will have to face another, and with each new step chances of infection drop dramatically”.
And last, but not least, your attention and your smarts are some of the best antiviruses out there. Pay attention before opening any mail or links received on social media websites, delete the suspicious ones.
Free wi-fi and its dangerous side
A Cabinet Office report of 2015, quoted by DailyMail UK, revealed more than half of people in the UK have fallen victim to cybercriminals. According to follow-up research by Hidemyass.com (HMA), nearly two thirds (59%) of people regularly use unsecured, or ‘open’ Wi-Fi hotspots with one in five (20%) doing so weekly or more. Moreover, a very worrying factor, among those who use these unsecured networks, 19 per cent log on to online banking and 31 per cent send emails and personal documents.
Being safe on free wi-fi:
-
- Ensure a network is genuine and choose it wisely: Check the name of the network with a shop worker. According to cnet.com, “it’s pretty easy for someone who wants to intercept your data in a man-in-the-middle attack to set up a network called “Free Wi-Fi” or any other variation that includes a nearby venue name, to make you think it’s a legitimate source”. Therefore, if you are connecting via Windows, make sure to turn off file sharing and mark the Wi-Fi connection as a public network. You can find this option in the Control Panel > Network and Sharing Center > Change Advanced Sharing Settings. Under the Public heading, turn off the file sharing toggle. You may also want to turn on the Windows Firewall when connecting to a public network if it’s not already activated. These settings are also found in Control Panel > Windows Firewall.
- Check the lock: Secure websites display a green padlock symbol, also known as Https. Make sure this is present when using a site that handles personal data and avoid accessing sensitive documents or pages using public Wi-Fi.
- Use a Virtual Private Network (VPN): Not all sites display the Https lock symbol, but a VPN will act as an intermediary between the device and the internet server. A VPN client encrypts traffic between your device and the VPN server, which means it’s much more difficult for an intruder to get to your data. SecurityKiss, CyberGhost or Disconnectme are some VPN services available that will help you.
- Don’t update your software or other apps, while on a public wi-fi. Keep your browser and internet-connected devices up to date with the latest versions, but make sure to do this on a trusted home or work network — not on public Wi-Fi. There have been instances of travelers being caught off guard when connecting to public or hotel Wi-Fi networks when their device prompts them to update a software package. If accepted by the user, malware was installed on the machine.
- Enable two-factor authentication. According to cnet.com, this is a good piece of advice on services such as Gmail, Twitter and Facebook. This way, even if someone does manage to steal your password when on public Wi-Fi, you have an added layer of protection. Moreover, as a general rule, try not to use the same password across multiple services.
- Downloading an app? Check permissions: Before installing, make sure apps can’t access unnecessary information. For example, a drawing app shouldn’t need a contacts list.
- Turn-off sharing. When you’re on a public network, you’ll want to turn these things off, as anyone can access them and, depending on your setup, some of that stuff probably isn’t even password protected.
- Automate Your Public Wi-Fi Security Settings. According to lifehacker.com, there are a few ways to automate the process so you automatically get extra protection when connected to a public Wi-Fi network. When you first connect to any given network on Windows, you’ll be asked whether you’re connecting to a network at your home, work, or if it’s public. Each of these choices will flip the switch on a preset list of settings. The public setting, naturally, will give you the most security. If you want more control, NetSetMan is a great program to customize your network profiles for different networks; you choose your IP address, DNS server, or even run scripts (opening the window for pretty much any action) every time you connect to one of your preset networks. “OS X doesn’t have these options built-in like Windows, but an app like ControlPlane can do a fair amount of customization. With it, you can turn on your firewall, turn off sharing, connect to a VPN, and a whole lot more, all depending on the network you’ve connected to,” adds lifehacker.com.
- Forget the network: When leaving a public network, don’t just log off, ask the device to forget the network so it doesn’t automatically log on when in range later.
Don’t be afraid of the cloud, most of your data is already out there
Afraid of storing your data on the cloud? Don’t. Just think at the fact that any email service you are using (Gmail, Yahoo, Hotmail etc.) is already using the cloud, so your data is backed-up up there. None of those emails you send and receive are actually taking up space on your local hard drive, but they are stored on the email providers’ servers: this is a form of cloud computing.
Actually, cloud storage means minimal downtime and it significantly reduces the possibility of losing data, because rather than storing it in one physical location, information is placed in several servers, in multiple locations. So if one server goes down, the data doesn’t disappear. Cloud storage is convenient, and with the right precautions, it’s about as secure as keeping the data on-site at all times.
According to cloud-lounge.org, many businesses large and small use cloud computing today either directly (e.g. Google or Amazon) or indirectly (e.g. Twitter) instead of traditional on-site alternatives. And there are a number of reasons why cloud computing is so widely used among businesses today: Reduction of costs (unlike on-site hosting the price of deploying applications in the cloud can be less due to lower hardware costs from more effective use of physical resources), universal access (remotely located employees can access applications and work via the internet), choice of applications (flexibility for cloud users to experiment and choose the best option for their needs), potential to be greener and more economical (the average amount of energy needed for a computational action carried out in the cloud is far less than the average amount for an on-site deployment), flexibility (allows users to switch applications easily and rapidly, using the one that suits their needs best).

Moreover, according to wired.com, the cloud offers better insight, helps collaboration between the members of the teams, drives better engagement (as cloud is often seen as the most effective means of forging a tighter link with the customer), its benefits are measurable and pay for themselves.
But, if after all of these you are still afraid of using it, remember that many cloud services offer additional security options on top of the basic packet and you have at your disposal several measures you can take in order to protect your data. Tim Maliyil, CEO and data-security architect for Las Vegas-based AlertBoot, explained some of them for entrepreneur.com:
- Encrypt everything. Any cloud service a startup uses should implement encryption on the server side. Even if the cloud infrastructure were to be compromised, a hacker would only be able to access encrypted gibberish and no data would be stolen.
- Have a strong password. While the death of the password as a security linchpin is long overdue, it’s still the easiest point of access for users and hackers. Be sure your passwords are at least 15 characters long and include numbers, letters and special characters if possible.
- Start early. The reason major chains such as Home Depot and Target tend to be susceptible to security breaches isn’t simply because they’re high-profile organizations. Larger, more complex companies have a harder time implementing comprehensive security solutions than do smaller, more nimble companies.
Put security protocols in place while the infrastructure is still manageable so security can scale with the company instead of playing catch-up. Additionally, if the company targets regulated industries such as health care, proof of meeting data-security-compliance requirements will be needed for conducting business.
Data breaches don’t so much reflect an inherent insecurity in cloud services as they do a problem with how the available measures are implemented. Cloud services have allowed startups to thrive and scale at a fraction of the cost of companies running their own server farms. Use cloud services to build end-to-end security so as to get back to focusing on the important things: the company’s products and customers.
Part of those piece of advice can be found also on Drew Hendricks of Inc.com’s list, from which we would also mention the following:
- Backing up sensitive files. While file sharing and syncing are effective ways to back up documents, they should not replace the use of external devices. By backing up files virtually and physically, you can all but guarantee your firm will have access to its data even in the event of system crashes or attacks.
- Separating personal from corporate data. Whether your business features a “Bring Your Own Device” (BYOD) culture or not, you need to communicate clearly with employees about what information can and cannot be stored on personal devices, as well as what encryption methods are required.
- Keep sensitive materials out of the cloud. Until cloud providers can offer comparable levels of security to what is available on an internal business server, they may not be worth the risk for some data.
Online identity protection – 10 simple tips
source: medibid
Up to 9 million Americans have their identities stolen each year according to the FTC , and at least 534 million personal records have been compromised since 2005 through attacks on the data bases of businesses, government bodies, institutions, and organizations. For some consumers, identity theft is an annoying inconvenience and they can quickly resolve their problems and restore their identity. For others, recovering their identity can cost hundreds, even thousands of dollars, take months to resolve, cause tremendous damage to their reputation, cause them to lose job opportunities, even influence the rejection of loan applications for school, homes or cars because would-be employers or loan companies see the damage on your credit scores.
In order to help you prevent these types of situations, here are some tips & tricks you should follow:
- Protect your computer and smartphone with strong, up-to-date security software. If your computer or phone is infected with malicious software, other safeguards are of little help because you’ve given the criminals the key to all your online actions. Also be sure that any operating system updates are installed.
- Learn to spot spam and scams. Though some phishing scams are easy to identify, other phishing attempts in email, Instant Messaging, on social networking sites, or websites can look very legitimate. The only way to never fall for phishing scam is to never click on a link that has been sent to you by someone you don’t know, looks suspicious or from a third party that you didn’t request the information from.
- Use strong passwords. Weak passwords are an identity thief’s dream – especially if you use the same password everywhere. You need passwords that are long (over 10 characters), strong (use upper and lower case letters, numbers and symbols), and that have nothing to do with your personal information (like name, age, birth date, pet)
- Use multiple passwords. Have more than one password for online accounts or – if it’s cracked – thieves will be able to gain access to all your private data at once.
- Freeze your credit. Criminals use stolen ID’s to open new lines of credit. You can thwart their efforts to use your identity by simply locking (called freezing) your credit so that no new credit can be given without additional information and controls.
- Monitor & review your credit scores and bank data. Look too see if there are new credit cards, loans or other transactions on your account that you are not aware of. If there are, take immediate steps to have these terminated and investigated.
- Only use reputable websites when making purchases. If you don’t know the reputation of a company that you want to purchase from, do your homework. How are they reviewed by other users? Do they use a secure, encrypted connection for personal and financial information?
- Stay alert. Watch for common signs of identity theft like:
- false information on your credit reports, including your personal numeric code, address(es), name or employer’s name.
- Missing bills or other mail. If your bills don’t arrive, or come late, contact your creditors. A missing bill may indicate that an ID thief has hijacked your account and changed your billing address to help hide the crime.
- Getting new credit cards sent to you that you didn’t apply for.
- Having a credit approval denied or being subjected to high interest rates for no apparent reason.
- Receiving calls or notices about past due bills for products or services you didn’t buy.
- Exclude important personal information from your social media profile. On Facebook, that means culling any ‘friends’ you don’t know, minimizing the details in your ‘About Me’ section and being selective about hitting the ‘like’ button, all of which will make you harder to find.source: backtoyourcountrynavigator
- Check your social media & phone privacy settings. Change all Facebook settings to “Friends Only” for all posts for a more secure profile. Facebook often makes changes to these settings and, when it does so, can even reset your secure settings. Moreover, turning your GPS location settings to “off” can also keep your family’s whereabouts more private.